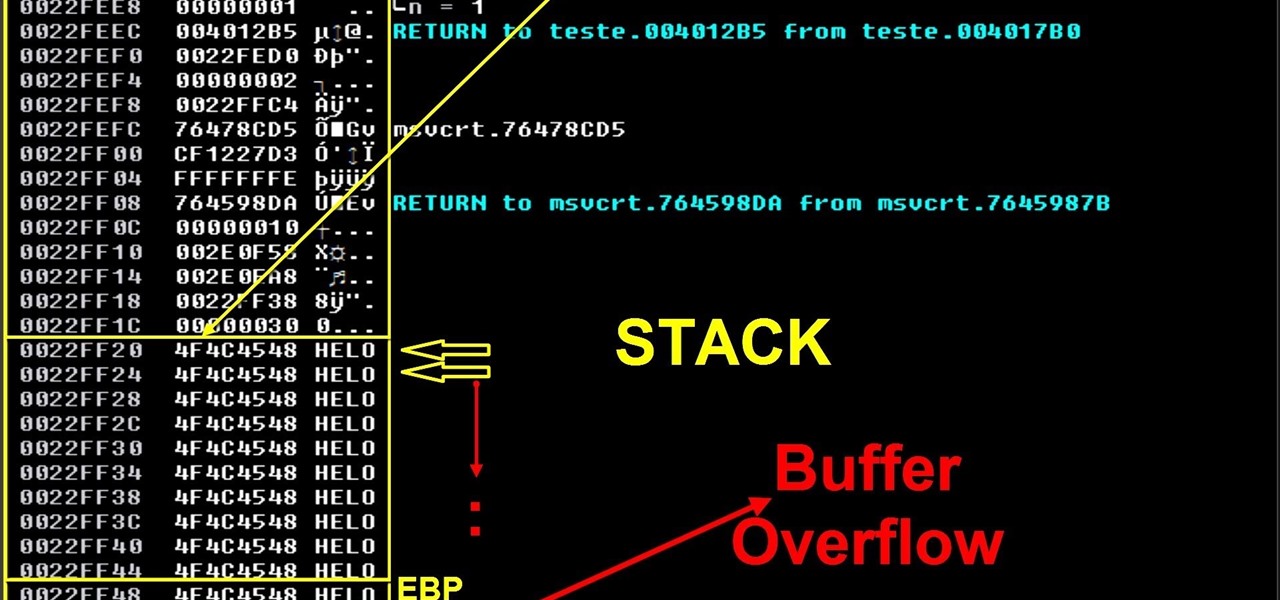
Find helpful customer reviews and review ratings for Hacking: The Art of Exploitation wCD at Amazon big O notation, how to analyze an algorithm, denial of service, exploit writing, and all sorts of cool hacker stuffz, sez everywun! just the right amount of code, and just the answers I was looking for as someone who really wants to know. The art of creating backdoors and exploits with Metasploit. there is no reason for an attacker to find and exploit vulnerable software. 10 (on outside or untrusted simulated environment) Tags: Hacking, Hacking Tools. Hacking is the art of creating problem solving, whether used to find an unconventional solution to a difficult problem or to exploit holes in sloppy programming. Many people call themselves hackers, but few have the strong technical foundation that The Art of Hacking is a series of video courses that is a complete guide to help you get up and running with your cybersecurity career. This GitHub repository has been created to provide supplemental material, tons of references, scripts, and code that help you build your own hacking environment. Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Jon Erickson Hacking: The Art of Exploitation Book Review The fine line between an exploit program and an exploit tool is a matter of finalization and recon figurability. an insightful book and definitely well worth a read if you're interested in learning the basic concepts of hacking and, specifically, how to exploit a Linux system. While other books merely show how to run existing exploits, Hacking: The Art of Exploitation broke ground as the first book to explain how hacking and software exploits work and how readers could d As you can see, our new Hacking Team exploit has been moved to the proper directory for use with Metasploit. If you don't have that directory, simply create it with mkdir. Step 3: Start Metasploit Hacking: The Art of Exploitation teaches the reader to think like the hacker writing the exploits so that he can learn to think for himself. And that is the essence of hacking. HACKING The Art Of Exploitation File marked as fake or malicious, links removed. Using BitTorrent is legal, downloading copyrighted material isnt. This video covers how to use the live Linux CD from the book, Hacking the Art of Exploitation, with an oracle virtual box EXTRA step! With the virtual bo i've got a question regarding the exploitnotesearch program. This program is only used to create a command string we finally call with the system() function to exploit the notesearch program that. buffer overflow exploit example from Hacking: The Art of Exploitation. Hello all this is a question regarding programs from the book Hacking the art of exploitation. here are the programs i am testing: notetaker. c Hacking the art of exploitation, sometimes don't work Share your knowledge at the LQ Wiki. Security cheat sheets for Ethical Hacking and Penetration Testing by sniferl4bs. This cheat sheet is especially for penetration testersCTF participantssecurity enthusiasts. New Exploit to 'Hack Android Phones Remotely' threatens Millions of Devices. HackingThe Art of Exploitation. 895 likes 1 talking about this. White Hat Hacking An exploit (from the English verb to exploit, meaning to use something to ones own advantage) is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). PRAISE FOR THE FIRST EDITION OF HACKING: THE ART OF EXPLOITATION Most complete tutorial on hacking techniques. Finally a book that does not Question: How Many Tech Books Should You Read Per Week to be Successful? Failed Normal Redux 25, 208 views I've been reading Hacking: The Art of Exploitation 2nd Ed. and I hit a part that's not explained clearly enough for me. In the section Writing to an Arbitrary Address Jon Erickson creates a November 28, 2017 in art, Exploit, Hacking, Information Gathering, Pentesting, Social Engineering HACKING: THE ART OF EXPLOITATION By JON ERICKSON The goal of this book is to share the art of hacking with everyone. Hacking: The Art of Exploitation 2nd Edition (HTAoE) by Jon Erickson is frequently considered a must read for those wanting to understand exploits and exploit development. So when I wanted to understand more about the exploit development side of security this was the first book I picked up. Archived security papers and articles in various languages. 1, 442 total entries prev 1 2 3 4 5 6 7 8 9 10 next. This repository contains the source code that comes from the book: Hacking The Art of Exploitation. The VM that this code runs on is an Ubuntubased Live Linux Distro. com Follow @dawidgolunski ExploitBox. io Interested in security vulns exploits? io A Playground Labs for security folks into hacking the art of exploitation Follow @ExploitBox Discovered by: Dawid Golunski CVE Release date. Art and Illustration; Audio and Music; CAD; Ethical Hacking: Exploits Course by: Malcolm Shore. the key to success in such a career is to really understand how malware is able to exploit. About The Exploit Database; History of ExploitDB; Introduction# # # # # Hi all, in this paper, we will guide you about methods to hacking into Windows system and linux system. Moreover, we also show the ways to use popular hacking tools, nmap and metasploit. Then use the G0d of Exploit suite. Jon Erickson liefert mit der nun verfgbaren deutschen Ausgabe der 2. amerikanischen Auflage Hacking: The Art of Exploitation die aktualisierte Version seiner HackerBibel: die technischen Grundlagen, und HardwareEinsicht als Ausgangsposition auch fr Unbedarfte. Art and Illustration; Audio and Music; CAD; What is an exploit? From the course: Ethical Hacking Learning about ethical hacking for exploits is part of the Malware competency from the. Primarily, hacking was used in the good old days for leaking information about systems and IT in general. If you're ready to dive in and learn the art, this article will share a few tips to help you get started. You can't truly exploit a program if you don't know assembly. Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Many people call themselves hackers. A comprehensive introduction to the techniques of exploitation and creative problemsolving methods commonly referred to as hacking, Hacking: The Art of Exploitation is for both technical and nontechnical people who are interested in computer security. It shows how hackers exploit programs and write exploits, instead of just how to run other people's exploits. Hacking: The Art of Exploitation, 2nd Edition by Jon Erickson Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Buy Hacking: The Art of Exploitation 2 by Jon Erickson (ISBN: ) from Amazon's Book Store. Everyday low prices and free delivery on eligible orders. The 6 Most Common Social Hacking Exploit Techniques Posted on January 11th, 2016 by Arthur Baxter When hackers breach even the most complicated security systems, they often do. hacking art of exploit Free Search and Download Torrents at search engine. Download Music, TV Shows, Movies, Anime, Software and more. This question is about the exploit for the program notesearch on pg 121 of the book Hacking: Art of Exploitation 2nd Edition. There is something I do not understand in the exploit: When the Sys Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Many people call themselves hackers Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Many people call themselves hackers, but few have the strong technical foundation needed to really push the envelope. The Paperback of the Hacking: The Art of Exploitation by Jon Erickson at Barnes Noble. This book dosn't just instruct you on running a program to create an exploit, it takes you into the anatomy of one, how it works, and shows you how to code it. You have probably heard of such hacking techniques as. The Art of Hacking certification is provided by NotSoSecure and is designed to assess candidates applied, handson skills against over 60 competencybased learning objectives Certification can only be achieved by completing the Art of Hacking Capture The Flag (CTF) An examination following completion of your Art of Hacking class; be it. So here is the list of all best hacking books free download in PDF format. Vulnerability Exploit website Hacking for Dummies; Web App Hacking (Hackers Handbook) hacking for dummies; hacking the art of exploitation; So above are the Download Best Free Hacking books. David Martinjak writes Hacking: The Art of Exploitation is authored by Jon Erickson and published by No Starch Press. It is the anticipated second edition of Erickson's earlier publication of the same title. I can't think of a way to summarize it without being overdramatic, so it will just be sai BACK TO legalhackers. com Follow @dawidgolunski ExploitBox. io Interested in security vulns exploits? io A Playground Labs for security. Start by marking Hacking: The Art of Exploitation as Want to Read: introduction to the techniques of exploitation and creative problemsolving methods commonly referred to as hacking. It shows how hackers exploit programs and write exploits, instead of just how to run other people's exploits..